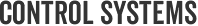What is Industrial Control Systems?
Authored by Gareth Pritchard, Azeem Aleem, Peter Tran
From the days of Slammer, Stuxnet, Shamoon, etc., to the recent Ukrainian (black energy) Power Grid and “Panel Shock” Attacks, we are witnessing a sophisticated surge in the attack domains across industrial control systems. The shift from legacy systems towards process control networks with connectivity around enterprise and Internet has created extensive backdoors exploit around the industrial control systems (ICS). We are seeing that organizations are not even aware of the device connectivity patterns inside and outside their ICS environment. Attacks through cloud service providers within ICS are on the rise, and there is a dire need of intelligence correlations and reporting mechanisms around SCADA attacks, through behavioral analytics.
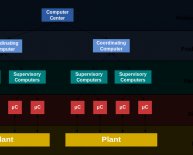
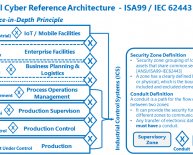
The media and general public usually refer to all ICS architectures as SCADA, and, while this is literally and technically incorrect – referring to the architecture as “Industrial Control System” is considered a safe catchall for all terms. when discussing critical infrastructure to avoid autocratic debates within various security groups.
In this series of upcoming blogs, we will discuss the vulnerabilities within the ICS systems, RSA SCADA domains and framework, and the mitigation techniques developed from our experience in the field. Our intention, through sharing these insights and concepts, is to recommend that organizations consider, and adopt, a holistic methodology.